The browser accessories can be a great way to enhance your productivity while browsing. The Chrome, the most popular browser there, supports a wide range of extensions, as well as other vineyard -based browsers. However, these extensions are not always useful. While many of them are useful in preventing ads, finding the best deals or verifying the rules errors, some can end up causing more harm than benefit.
I am recently It was reported on a set of harmful extensions This was the stealing of user data, and now a new report informed 35 with other reports. These browser extensions require unnecessary permissions and were reported to collect and share everything you do online.
Join the free “Cyberguy Report”: Get expert advice experts, critical safety alerts and exclusive deals, as well as immediate access to my country free “The ultimate survival guide “ When registering!
A man uses Google Chrome Browser on his laptop. (Cyberguy “Knutsson)
Surface extensions in the wilderness
accident Investigation by John ToknerThe founder of Secure Annex, revealed concerns about 35 chrome extensions, which constitutes the risk of possible privacy and security risks. These extensions, which were inserted into the Chrome store on the web, were installed collectively on more than 4 million times.
Many of these simple extensions provided themselves as tools to help search, ban advertisements, safety monitor, or wipe the extension, but they participated in a connection with one field that is not used, indicating coordinated behavior. All of them use the same code patterns, connect some servers and require the same list of sensitive systems permissions, including the ability to interact with web traffic on all of the URLs that have been visited, access to cookies, and managing the browser tab and implementing textual programs.
The most important is that at least 10 of these extensions carry a “distinctive” badge of Google, which means examination for the merit of confidence. This raises questions about the Google review process, as the emblem suggests compliance with the high standards of the user experience, privacy and safety.

Pirates at work. (Cyberguy “Knutsson)
How to remain hidden and hide your number when calling someone
Why are these extensions bad?
The main concern is the level of access to these extensions that you require quietly and how to use them. With permissions to read the tabs, access to cookies, intercept web requests and inject textual software in pages, they can monitor almost everything you do in your browser. This includes tracking your browsing activity, monitoring login sessions and changing the content of the web sites you visit, all without your knowledge.
These extensions are not simply wrong tools. It seems intentionally designed with observation. Many of their configuration data is locally, which allows remote servers to update their behavior at any time. This setting is commonly seen in spyware, where changes can be made after installation without alerting the user. The symbol is very full, which makes it difficult for researchers to understand what the extensions already do.
In some cases, the additions seem to do nothing at all when clicking on them. However, they continue to send data in the background. For example, protecting the extension of the fire shield remained inactive until the researcher manually turned it with a specific extension identifier. Only then started to transfer browsing and other data, revealing the behavior that will be difficult for the average user to discover.

A person running on a laptop. (Cyberguy “Knutsson)
Mescape programs display 3.9 billion passwords in the threat of huge cybersecurity
35 extensions to delete now
35 public extensions can be searched on the Chrome store on the web, which means that it can only be installed through direct URL addresses. The full list of additions is:
- Choose your chrome tools
- Kruma safety shield fire
- Safe search for chrome
- Protect the extension of the fire shield
- Browser examination for chrome by doctor
- Protecto for chrome
- Unbiaded research by Protecto
- Securing your browser
- Web privacy assistant
- Securify Kid Protection
- Ping Search by Securify
- Browse safely for chrome
- It is better to browse Securitysearch
- Check my bills for chrome
- The safety of Chrome
- Multisearch of chrome
- Global search for chrome
- Find the map for chrome
- Watch a tower overview
- Virial shield
- On the site I am looking for chrome
- Chrome privacy guard
- Search Yahoo by ghost
- Special search for chrome
- Total safety for chrome
- Data shield for chrome
- Monitor the browser for chrome
- Searching for cost for chrome
- Web results for chromium
- CUPONOMIA – Call and Cash
- Security for Chrome
- Securify Sucurify Advanced Web Protection
- Search for news about Chrome
- Securybrowse for chromium
- Browse safely for chrome
How to remove an extension of Google Chrome on the desktop
If you have installed one of the above extensions on your browser, remove it as soon as possible. To remove an extension of Google Chrome on a desktop, follow these steps:
- Open chrome Click Icon resembling a piece of puzzle. You will find it in the right upper corner of the browser
- You can see all the active extensions now. Click Three icon Besides the extension you want to remove and define Raise from chrome
- Click Remove To confirm
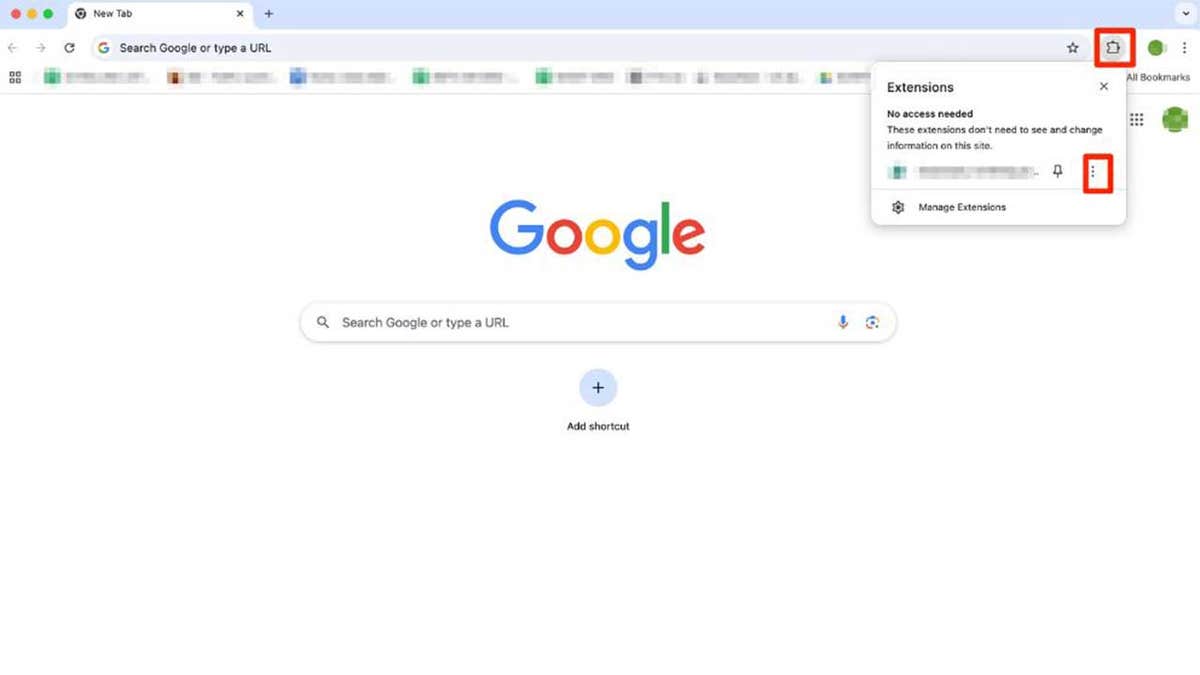
Steps to remove an extension of Google Chrome. (Cyberguy “Knutsson)
How to remove your private data from the Internet
5 ways to stay safe from slow extensions
If you are concerned about the above extensions, here are five ways to protect your sensitive information and keep your privacy online.
1) Keep your browser updated: Chrome gets regular updates that get rid of most security problems. Make sure to run the automatic updates of your browser (for example, Chrome, Firefox, Edge), so you are always running the latest version without thinking about it. See my guide to Maintain update your devices and applications For more information.
2) Installing the extensions only from reliable sources: Official browser stores such as the Chrome store are available on the web rules and a survey to arrest bad actors. It is not perfect, but it is still a better option when compared to a random website. The extensions are likely to hide unknown web sites, third -party downloads, harmful programs or spyware.
3) You have a strong anti -virus program: Fighting good viruses can warn you before installing harmful programs, such as false browser extensions. It can also alert you to reduce emails and ransom fraud, which helps to maintain your personal information and digital assets safe. Get the best winners of the Virus Control Protection 2025 for Windows, Mac, Android and iOS devices.
4) doubt the extensions that require unnecessary access: Some extensions intentionally exceeded. The calculator that asks about your browsing log or the weather application that wants your login data is a huge red sign.
Before installation, ask, “Does this permission coincide with the extension function?” If the answer is no, do not prove it. Watch out for wide permissions such as “Read and Change all your data on the web sites you visit” unless it is clearly justified (for example, password manager). If the update suddenly added new permission requests, get the reason. It may mean that the extension has been sold or penetrated.
5) Change your passwords and do them safely: If you have saved passwords in your browser (for example, via Chrome or “password saving” router), these accreditation data may be at risk if a harmful extension is installed. These built -in managers store passwords locally, in a Google, Microsoft, or Firefox account, and the hacked browser can give bad actors a way.
This does not usually apply to the accessories of the customized password manager, which independently codes your data and does not depend on the storage of the browser. However, if you are not sure if an extension has been hacked, it is always intelligent to update the main password and enable dual -factor authentication.
For the maximum safety, change the most important passwords (email, bank, shopping and cloud services) from a different and safe device, such as your phone or another computer, as the suspicious extension has never been installed. Avoid using the same browser that may be displayed. Then think about switching to the password manager to create and store unique entry records. I have reviewed the best options in my country The best password managers from 2025 evidence. Learn any one to better fit your needs.
Court Kisa Curt
The fact that many of these extensions carried a “distinctive” badge of Google should serve as a awakening call. It indicates a dangerous decrease in censorship and raises concerns about the comprehensiveness of the process of actually reviewing Chrome. When millions of users install spyware without knowing the impression that it has been examined and approved, the problem is no longer the bad actors. It reflects a deeper failure within the same platform. Google needs stronger responsibility by improving transparency and tightening their review standards.
Do you think that the browser makers such as Google should be more responsible for what is published in their stores? Let’s know through our writing in Cyberguy.com/contact
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter
Ask Kurt a question or tell us about the stories you want to cover.
Follow Court on his social channels:
Answers to the most amazing Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.
